Hi, Minions:
This is another
article, one of those that, for one reason or another, 'choke' for various
reasons. I had it pending, on my 'ToDo' list, half completed, for a long, long
time. And it's for that reason, because a lot of time has passed, that I've
restarted all those tests that I had half completed. Because the working
environment changes, because the systems change.
You could say that
this article came up by chance, a very long time ago... although it has some
relation with another article that I took up, also, a long time ago, and that I
published under the title of 'One
byte makes the difference: MFT Resident File'.
Introduction
We must know and
understand how the systems we are analysing behave. There are a multitude of
characteristics in them. These characteristics may be known or may yet be
'discovered'. Or, even, it may be the case that they are presented in some
versions and not in others, as it happens, for example, with the case of the
content I published in the article 'Windows
and its anti-forensic side, (Plug and Play Cleanup and setupapi[.]dev)'.
Some of those features may be recent or may have been there all your life. Some
of these features may have a strong impact on a forensic analysis and some of
these features may not have a serious impact on certain types of analysis. But that's something we won't get to know if we
can't understand how those features work in systems. It is important to
have a deep understanding of systems, as Harlan Carvey mentioned in an
article he published on May 8, 2019, (Deep
Knowledge, and the Pursuit Thereof).
There are times
when we are so focused on a task that, despite observing strange behaviour in
the work environment, we do not pay the
attention it deserves because, apparently, it has nothing to do with the
task we are carrying out at the time.
It's happened to
me, and it's going to happen to me. And, surely, it has happened to you and it
will happen to you.
Big mistake.
The feature I
want to talk to you about today is the tunnelling
of the file system. You're probably familiar with this feature, or maybe
you're not familiar with it at all. In any case, I'm sure you've seen it on
more than one occasion.
"It's important to have
a thorough understanding of systems, but it's impossible to know everything
about them.”
So, as Brett
Shavers rightly says in the article he published under the title "Don't
look back. Try to keep up. This is #DFIR."
"When you search for an
answer and find it, retaining what you learn is much better than posting a
question in a forum and waiting for someone to provide the answer."
The importance
of documentation
It is vital to document yourself before starting a
job.
File system tunneling is considered by some analysts to be a "somewhat obscure" feature of
Windows. This feature is that when
you delete a file and create another one, with the same name and in the same
path, the new file created inherits the same creation date as the file that has
been deleted. This happens if it is done within a certain time, (according to some articles I have been
reading, that time can be up to 15 seconds, by default). That is, you
have to give some specific conditions
to be able to observe how this functionality
reuses some metadata from another file.
"If we don't know these
'special' characteristics, we can get confused."
By not knowing
this type of characteristics, we fall into confusion for not being able to give
an answer, for not being able to explain, the reason for this peculiarity.
I've read and
studied the articles I've found on this subject. Let's do some chronology!
Some very
interesting articles have been written on this topic, although the original Microsoft documentation
that mentions this feature, and that those other articles reference, is no longer available, (http://support.microsoft.com/?kbid=172190).
(I asked the Infosec and DFIR
community, but no one seems to have the content of that article, since no one has ever responded to me). So,
right now, there is no official documentation about it. I hate that official
documentation is missing.
"Lack of documentation
increases confusion."
Luckily, Dan O'Day was
kind enough to keep some of the content of some of those 'lost' items in his GitHub
repository.
It seems that
this article from Microsoft mentioned that both NTFS and FAT file systems have
this peculiarity to create tunnels.
I quote from the filesystem tunneling content that Dan copied into his
repository and which has been mentioned by other articles as well:
"The Microsoft Windows
products listed at the beginning of this article contain file system tunneling
capabilities to allow compatibility with programs that rely on file systems to
maintain file meta-information for a short period of time.
"When a file is deleted
from a directory, (rename or delete), its short/long name pair and the time of
creation are saved in a cache, along with the name that has been deleted. When
a file is added to a directory, (rename or create), the cache is searched for
information to restore. The cache is effective for each instance of a given
directory. If a directory is deleted, the corresponding cache is removed."
"The idea is to mimic
the behavior that MS-DOS programs expect when they use the secure storage
method. They copy the changed data to a temporary file, delete the original and
rename the temporary to the original. This should look like the original file
when it is complete. Windows tunnels through the FAT and NTFS file systems to
ensure that the long/short file names are preserved when 16-bit applications
perform this secure storage operation.”
"The tunnel cache time
can be adjusted from the default time of 15 seconds, or if the tunnel
capabilities are not desirable, it can be turned off by adding a value in the
Windows Registry.”
"If tunneling is
disabled, applications using this secure storage method may lose the name they
do not know, usually LFN, and rediscovery of the shortcut targets could be
affected, as the creation timestamps cannot remain constant for files handled
by such applications. Maintaining the creation timestamp is possible in the
absence of tunneling if an application is smart enough. The same is not true
for long file names."
"...allow compatibility
with programs that rely on file systems to maintain file meta-information for a
short period of time. This occurs after deleting or renaming and recreating a
new directory entry with that meta-information, (if a creation or renaming occurs
that causes a file with that name to appear again in a short period of
time)".
……….
File system metadata is always cached, as you can read in this article
from Microsoft's official site.
In this other
article by Microsoft, dated July 15, 2005, (The apocryphal
history of file system tunnelling), which already mentions the
creation of tunnels in file systems, the reason for tunneling is explained,
mentioning that this feature was already
implemented in Windows 95.
I can't help but
get excited... So much nostalgia... Windows 95...
This article
also mentions that after deleting a file
with a long file name, the file generated later, within a certain time, with
the same name and identical location, will inherit, in addition to the creation
date, the same short
file name as the deleted file.
The last
sentence of that article caught my attention very much:
"Fragments of
information about recently deleted or renamed files are stored in data structures
called 'quarks'.”
That is,
according to this Microsoft article, during
the tunneling effect some of the information in the affected file is
temporarily saved.
Looking for
information about this, I found an article published on August 22, 2007, (Windows
Date Created Timestamp strangeness), which says that Windows caches the timestamp of the deleted
file for some time, and that this time can be up to 8 minutes.
On April 11,
2010, Harlan already started to publish material related to this
file system tunneling functionality. As mentioned by Harlan in that article,
under normal circumstances, timestamps,
(via timelines), already pose some
difficulty in analysis. If you add to that difficulty more elements that
are perhaps unknown... 'Turn off and let's go!
It is mentioned
in another article, published on 7 February 2012, (File
System Tunneling in Windows), that tunneling is related to the fact
that some programs using the secure
storage method copy the modified data to a temporary file before deleting the
original file and rename the temporary file with the original file name.
File system tunneling can be disabled and can also be
assigned a specific time, given in seconds. The first article I've seen that mentions this,
besides the extract from the official documentation that Dan kept, is one that
was published on February 24, 2014, (Microsoft
Windows File System Tunneling). This article says that these two
operations can be carried out by adding a key pair to the Windows Registry:
To disable the file system tunneling,
simply add the key
“HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\FileSystem\MaximumTunnelEntries”
And assign that
key a value of '0'.
To modify the
time of the tunneling it would be enough to add the key
“HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\FileSystem\MaximumTunnelEntryAgeInSeconds”
And assign that
key a set value in seconds.
Harlan also
published another very interesting article on this subject, with interesting
evidence, on July 22, 2014, (File
system ops, effects on MFT records). According to the evidence he
presented, he concluded that during the
file system tunneling, the original file record in the MFT is marked as
'deleted' and that a new record is assigned to the new file created during that
tunneling. You could also see that $UsnJrnl
contains entries showing that a file system tunneling has taken place.
On August 2,
2013, Blazer
Catzen published in David Cowen's Blog a good
presentation on this topic, which you can
download from his Google site.
I couldn't find
any other material that caught my attention until Hideaki Ihara first published an
article on October 12, 2018, (File System
Tunneling and E:\), where he performs some tunneling tests on a USB
device. Hideaki published another article, on October 19, 2018, (File System
Tunneling and C:\), performing the same tests on a local disk.
Finally, more
recently I found another interesting article, published on April 13, 2019, (File
System Tunneling in Windows), which is very well explained, with
interesting proofs, and which links to a very interesting PDF document, which
you can download
from Microsoft's official site. This document, titled "File
System Behavior in the Microsoft Windows Environment", mentions, among
other things, that FAT, NTFS and exFAT file systems support file tunnelling,
while the UDF file system does not support file tunnelling.
And this is the
extent of the documentation I have followed in order to study and understand
tunneling. But... Even with all that has been written, I have some doubts.
Doubts that I'm going to try to clear up on my own.
The test environment
For the tests I
have carried out, I have chosen to use a Windows
10 system, in its version 18363,
and a Windows 10 system, in its version 17763. Both systems have been
virtualized with VirtualBox,
assigning 8 GB of RAM and 4 processors to each of them.
You can download
Microsoft Windows virtual machines for virtualized environments from their
official site at the following links:
- https://developer.microsoft.com/en-us/microsoft-edge/tools/vms/
- https://developer.microsoft.com/es-es/windows/downloads/virtual-machines/
On each of the
virtualized Windows 10 systems I performed a number of actions. More
specifically, I can say that I divided the tests into the following five actions
for each system:
- CCDR - Create a file 'A' in a folder; create a file
'B', in the same folder; delete file 'A'; and rename file 'B' as 'A'.
- CCRR - Create a file 'A' in a folder; create a file
'B', in the same folder; rename file 'A' as 'C'; and rename file 'B' as 'A
- CDC - Create a file 'A' in a folder; delete file
'A'; and recreate a file 'A', in the same folder
- CMC - Create an 'A' file in a folder; move the 'A'
file to another folder; and recreate an 'A' file, in the same folder.
- CRC - Create a file 'A' in a folder; rename file 'A'
as 'B'; and create a file 'A', in the same folder.
The meaning of
the abbreviations is:
- C = Create
- D = Delete
- R = Rename
- M = Move
In turn, each of
these actions has been carried out under a series of conditions, combined with
each other:
- A waiting time
of 1400 milliseconds.
- A waiting time
of 1500 milliseconds.
- A waiting time
of 1600 milliseconds.
- Long file names.
- Short file names.
- A file size of
512 bytes.
- A file size of
4096 bytes.
At the same
time, all these tests have been executed:
- On a system
with a default configuration.
- On a system
with tunneling disabled.
- On a system
with a certain tunneling value.
- On a system
with a maximum tunneling value.
- In a system
with the creation of short names
disabled.
- In a system
with timestamp updating disabled.
These are just
some of the possible combinations I've come up with, but there's more. Even so,
you can calculate the total number of runs I have carried out, on both systems,
and get an idea of the time spent on all these tests, and their subsequent
analysis. You can rest assured, because
I will not expose all the results I have obtained in the tests. I'll just stick
to those that I think are of interest. But don't miss out on a good cup of
coffee ;)
Each of the actions, described above, has been
automated by a small script in PowerShell, with the following structure
During the
execution of each one of these scripts I have proceeded to extract the files '$MFT' and '$LogFile', with the OSForensics
tool, in its portable version, (You can use any other, like FTK
Imager Lite). The extraction of these files has been carried out
just after the creation of the first file and just after the execution of the
script. That is, both elements have been extracted twice, for each execution,
in order to compare the before and after
information.
Similarly, I have
allowed a total of 300 seconds to elapse, just after preparing the files for
the tunnel effect. 300 seconds is more than enough time for the extraction of
the necessary elements, for its later analysis, and to carry out some
screenshots with the tool Active@ Disk Editor,
in order to study the different attributes and metadata of each one of the
treated files.
Regarding the
processing of the extracted '$MFT' and '$LogFile' files, I have chosen to use
the FTE
and MFTECmd tools for
the analysis of the '$MFT', (for the
contrasting data and other weird things I like to do), and the LogFileParser
tool for the analysis of the '$LogFile'.
A short version...
Thank you, statistics!! I have been able to verify, thanks to the statistics,
that you will not spend more than two minutes reading any of my articles. That's
why I'm going to present now, and not at the end, as I usually do, a brief
summary of the work done.
The file system
tunneling will become visible, according
to my tests, if the actions are carried out within 15000 milliseconds,
on a system with a default configuration. All this, regardless of the size of
the file and the type of file name, with one exception.
Tunneling is
generated when:
- A file 'A' is
created in the folder 'X', a file 'B' is created in the folder 'X', file 'A' is
deleted and file 'B' is renamed to 'A'.
- A file 'A' is
created in the folder 'X', a file 'B' is created in the folder 'X', file 'A' is
renamed as 'C' and file 'B' is renamed as 'A'.
- A file 'A' is
created in the folder 'X', file 'A' is deleted, another file 'A' is created in
the folder 'X'.
- A file 'A' is
created in the folder 'X', file 'A' is moved to the folder 'Z' and another file
'A' is created in the folder 'X'.
- A file 'A' is
created in the folder 'X', the file 'A' is renamed as 'B' and another file 'A'
is created in the folder 'X'.
Of the cases
mentioned above, the only exception where the tunnel effect will not be
generated is in the case of combining a long file name with its short name
equivalent.
If file system
tunneling is disabled, it will not occur under any conditions, except for the
very action of overwriting a file.
You can
customize the file system tunneling time, up to a maximum, determined in
seconds.
The maximum time
the file system can be tunnelled is 71000 milliseconds.
Disabling the
creation of short file names, (8.3), also disables the tunnelling of the file
system, since tunnelling is based on such names.
Disabling the
update of timestamps does not affect the tunnel effect. That is, even if this
function is disabled, it is still generated.
Not in all cases
a new entry is assigned in the MFT for the file causing the tunnel effect. In
fact, in those actions that imply the elimination of file 'A', the entry in the
MFT is reused, for file 'B'. This has been seen by disabling the file system
tunneling, by disabling the creation of short names, (8.3), and in the case of
file overwriting.
We will not
always find, when a tunnel effect is generated, a discordance in the creation
dates of the attributes 'SI' and 'FN'. In fact, there will be occasions when we
must base the study on the discordance of dates within the 'SI' attribute.
The answer to
the explanation of a tunnel effect will be found in the analysis of the
'$LogFile' file.
Testing in a Default System
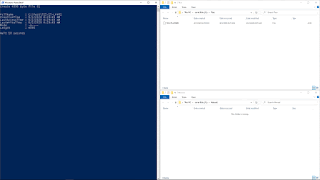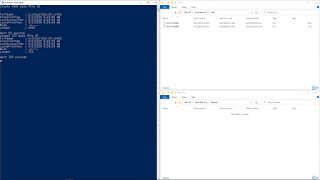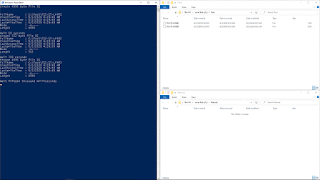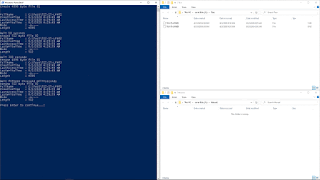
CCDR
Create a file 'A' in a folder; create a file 'B', in
the same folder; delete file 'A'; and rename file 'B' as 'A
- Create a 512-byte 'A' file with a long name
- Create a 512-byte 'B' file with a long name
- Delete the 'A' file
- Set a timeout of 14000 milliseconds
- Rename file 'B' to 'A
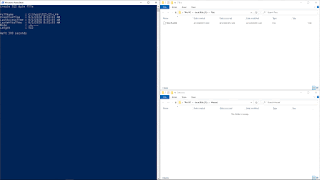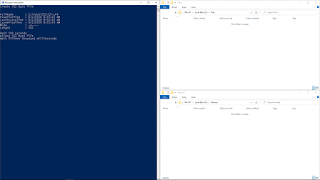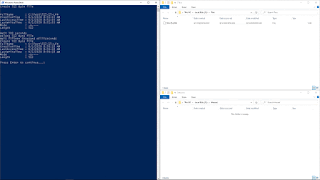
In this test, as
you can see in the previous animated image, a file with the long name
'512-14-LFN01' was created in the system in the 'Test' folder, on 29-05-2020 at
16:12:45. This file was assigned the entry number 93994 in the MFT. After
waiting 10 seconds, a second file was created with the long name
'512-14-LFN02', in the same folder, at 16:12:55. This second file was assigned
entry number 93996 in the MFT.
After waiting
300 seconds, the file was deleted with the name '512-14-LFN01' and, after a
wait of 14000 milliseconds, the file was renamed '512-14-LFN02' to
'512-14-LFN01'.
As you can see
from the above table extracts, the file '512-14-LFN01', which occupied the
entry number 93994 in the MFT, has been deleted and, the file '512-14-LFN02',
which occupies the entry 93996 in the MFT, has now been renamed '512-14-LFN01'.
Regarding the
time stamps, the renamed file was created on 29-05-2020 at 16:12:55, (in
green). However, as you can see, by renaming it with the same file name as the
deleted one, it acquires the creation date of that deleted file, at 16:12:45,
(in red), showing, in the other timestamps, the original creation date of the
file. This indicates that, in this case, with a waiting time of 14000
milliseconds, a tunnel effect has been generated.
Create a file 'A' in a folder; create a file 'B', in
the same folder; delete file 'A'; and rename file 'B' as 'A
- Create a 512-byte 'A' file with a long name
- Create a 512-byte 'B' file with a long name
- Delete the 'A' file
- Set a timeout of 15000 milliseconds
- Rename file 'B' to 'A
In this test, as
you can see in the previous animated image, a file with the long name
'512-15-LFN01' was created in the system in the 'Test' folder, on 01-06-2020 at
10:23:22. This file was assigned the entry number 93893 in the MFT. After
waiting 10 seconds, a second file was created with the long name
'512-15-LFN02', in the same folder, at 10:23:32. This second file was assigned
entry number 94000 in the MFT.
After waiting
300 seconds, the file was deleted with the name '512-15-LFN01' and, after a
wait of 15000 milliseconds, the file was renamed '512-15-LFN02' to
'512-15-LFN01'.
As you can see
from the above table extracts, the file '512-15-LFN01', which occupied the
entry number 93893 in the MFT, has been deleted and, the file '512-15-LFN02',
which occupies the entry 94000 in the MFT, has now been renamed '512-15-LFN01'.
As far as time
stamps are concerned, in both cases the original dates are shown for each of
the two files, so, with a timeout of 15000 milliseconds, no tunnel effect has
been generated.
Create a file 'A' in a folder; create a file 'B', in
the same folder; delete file 'A'; and rename file 'B' as 'A
- Create a 512-byte 'A' file with a long name
- Create a 512-byte 'B' file with a short name
- Delete the 'A' file
- Set a timeout of 14000 milliseconds
- Rename file 'B' to 'A
In this test, as
you can see in the previous animated image, a file with the long name
'512-14-LFN01' was created in the system in the 'Test' folder, on 30-05-2020 at
15:05:08. This file was assigned the entry number 93893 in the MFT. After
waiting 10 seconds, a second file with the short name '512-14~2', which is the
equivalent of a short name 8.3, was created in the same folder at 15:05:18.
This second file was assigned the entry number 93996 in the MFT.
After waiting
for 300 seconds, the file was deleted with the name '512-14-LFN01' and, after a
wait of 14000 milliseconds, the file '512-14~2' was renamed to '512-14~2',
which is the equivalent of the short name 8.3 of the file '512-14-LFN01'.
As you can see
from the above table extracts, the file '512-14-LFN01', which occupied the
entry number 93893 in the MFT, has been deleted and, the file '512-14~2', which
occupies the entry 93996 in the MFT, has now been renamed '512-14~1'.
Regarding the time
stamps, in both cases the original dates are shown for each of the two files,
so in this case, with a waiting time of 14000 milliseconds, no tunnel effect
has been generated.
Create a file 'A' in a folder; create a file 'B', in
the same folder; delete file 'A'; and rename file 'B' as 'A
- Create a 512-byte 'A' file with a short name
- Create a 512-byte 'B' file with a short name
- Delete the 'A' file
- Set a timeout of 14000 milliseconds
- Rename file 'B' to 'A
In this test, as
you can see in the previous animated image, a file with the short name
'512-14~1' was created in the system in the 'Test' folder, on 01-06-2020 at
05:26:59. This file was assigned the entry number 93893 in the MFT. After
waiting for 10 seconds, a second file with the long name '512-14~2' was created
in the same folder at 05:27:09.
After waiting
300 seconds, the file was deleted with the name '512-14~1' and after a wait of
14000 milliseconds, the file was renamed '512-14~2' to '512-14~1'.
As you can see
from the table extracts above, the file '512-14~1', which originally occupied
the entry number 93893, is no longer available in the MFT, as that entry has
been replaced by another one that now belongs to the file 'ht_settings.ini',
from the Active Disk Editor application, at 05:33:08. On the other hand, the
file '512-14~2', which occupies the 94000 entry in the MFT, has now been
renamed '512-14~1'.
As far as
timestamps are concerned, the renamed file was created on 01-06-2020 at
05:27:09, (in green). However, as you can see, when you rename it with the same
file name as the deleted one, it acquires the creation date of that deleted
file, at 05:26:59, (in red), showing, in the other timestamps, the original
creation date of the file. This indicates that, in this case, with a waiting
time of 14000 milliseconds, a tunnel effect has been generated.
Create a file 'A' in a folder; create a file 'B', in
the same folder; delete file 'A'; and rename file 'B' as 'A
- Create a 512-byte 'A' file with a short name
- Create a 512-byte 'B' file with a short name
- Delete the 'A' file
- Set a timeout of 15000 milliseconds
- Rename file 'B' to 'A
In this test, as
you can see in the previous animated image, a file with the short name
'512-15~1' was created in the system in the 'Test' folder, on 02-06-2020 at
09:09:28. This file was assigned the entry number 93893 in the MFT. After
waiting for 10 seconds, a second file with the short name '512-15~1' was
created in the same folder at 09:09:38. This second file was assigned the entry
number 94000 in the MFT.
After waiting
300 seconds, the file was deleted with the name '512-15~1' and after a wait of
15000 milliseconds, the file was renamed '512-15~2' to '512-15~1'.
As you can see
from the above table excerpts, the file '512-15~1', which originally occupied
the entry number 93893, is no longer available in the MFT, as that entry has
been replaced by another one that now belongs to the file 'ht_settings.ini',
from the Active Disk Editor application, at 09:15:42. On the other hand, the
file '512-15~2', which occupies the entry 94000 in the MFT, has now been
renamed '512-15~1'.
As far as time
stamps are concerned, in both cases the original dates for the file '512-15~1'
are shown, so in this case, with a timeout of 15000 milliseconds, no tunnel
effect has been generated.
Create a file 'A' in a folder; create a file 'B', in
the same folder; delete file 'A'; and rename file 'B' as 'A
- Create a 512-byte 'A' file with a long name
- Create a 4096 byte 'B' file with a long name
- Delete the 'A' file
- Set a timeout of 14000 milliseconds
- Rename file 'B' to 'A
In this test, as
you can see in the previous animated image, a file with the long name
'512-14-LFN01' was created in the system in the 'Test' folder, on 31-05-2020 at
14:20:22. This file was assigned the entry number 93893 in the MFT. After
waiting 10 seconds, a second file was created with the long name
'512-14-LFN02', in the same folder, at 14:20:32. This second file was assigned
entry number 94000 in the MFT.
After waiting
300 seconds, the file was deleted with the name '512-14-LFN01' and, after a
wait of 14000 milliseconds, the file was renamed '512-14-LFN02' to
'512-14-LFN01'.
As you can see
from the above table extracts, the file '512-14-LFN01', which occupied the
entry number 93893 in the MFT, has been deleted and, the file '512-14-LFN02',
which occupies the entry 94000 in the MFT, has now been renamed '512-14-LFN01'.
As far as time
stamps are concerned, the renamed file was created on 31-05-2020 at 14:20:32,
(in green). However, as you can see, by renaming it with the same file name as
the deleted one, it acquires the creation date of that deleted file, at
14:20:22, (in red), showing, in the other timestamps, the original creation
date of the file. This indicates that, in this case, with a waiting time of
14000 milliseconds, a tunnel effect has been generated.
Create a file 'A' in a folder; create a file 'B', in
the same folder; delete file 'A'; and rename file 'B' as 'A
- Create a 512-byte 'A' file with a long name
- Create a 4096 byte 'B' file with a long name
- Delete the 'A' file
- Set a timeout of 15000 milliseconds
- Rename file 'B' to 'A
In this test, as
you can see in the previous animated image, a file with the long name
'512-15-LFN01' was created in the system in the 'Test' folder, on 02-06-2020 at
18:23:35. This file was assigned the entry number 93893 in the MFT. After
waiting 10 seconds, a second file with the long name '512-15-LFN02' was created
in the same folder at 18:23:46. This second file was assigned entry number
94000 in the MFT.
After waiting
300 seconds, the file was deleted with the name '512-14-LFN01' and, after a
wait of 15000 milliseconds, the file was renamed '512-14-LFN02' to
'512-14-LFN01'.
As you can see
from the extracts of the previous tables, the file '512-15-LFN01', which
originally occupied the entry number 93893, is no longer available in the MFT,
as that entry has been replaced by another one that now belongs to the file
'ht_settings. ini', from the Active Disk Editor application, at 18:30:02. On
the other hand, the file '512-15-LFN02', which occupies the 94000 entry in the
MFT, has now been renamed '512-15-LFN01'.
Regarding the
timestamps, in both cases the original dates for the file '512-15-LFN01' are
shown, so in this case, with a timeout of 15000 milliseconds, no tunnel effect
has been generated.
Create a file 'A' in a folder; create a file 'B', in
the same folder; delete file 'A'; and rename file 'B' as 'A
- Create a 4096 byte 'A' file with a long name
- Create a 512-byte 'B' file with a long name
- Delete the 'A' file
- Set a timeout of 14000 milliseconds
- Rename file 'B' to 'A
In this test, as
you can see in the previous animated image, a file with the long name
'4096_512_14_Seconds01' was created in the system in the 'Test' folder, on
02-06-2020 at 09:18:09. After waiting 10 seconds, a second file was created
with the long name '4096_512_14_Seconds02', in the same folder, at 09:18:19.
This second file was assigned entry number 94001 in the MFT.
After waiting
300 seconds, the file was deleted with the name '4096_512_14_Seconds01' and,
after a wait of 14000 milliseconds, the file '4096_512_14_Seconds02' was
renamed to '4096_512_14_Seconds01'.
As you can see
from the above table extracts, the file '4096_512_14_Seconds01', which occupied
the entry number 93893 in the MFT, has been deleted and, the file
'4096_512_14_Seconds02', which occupies the entry 94001 in the MFT, has now
been renamed '4096_512_14_Seconds01'.
Regarding the
time stamps, the renamed file was created on 02-06-2020 at 09:18:19, (in
green). However, as you can see, when you rename it with the same file name as the
deleted one, it acquires the creation date of that deleted file, at 09:18:09,
(in red), showing, in the other timestamps, the original creation date of the
file. This indicates that, in this case, with a waiting time of 14000
milliseconds, a tunnel effect has been generated.
Create a file 'A' in a folder; create a file 'B', in
the same folder; delete file 'A'; and rename file 'B' as 'A
- Create a 512-byte 'A' file with a long name
- Create a 512-byte 'B' file with a long name
- Delete the 'A' file
- Set a timeout of 15000 milliseconds
- Rename file 'B' to 'A
In this test, as
you can see in the previous animated image, a file with the long name
'4096_512_15_Seconds01' was created in the system in the 'Test' folder, on
02-06-2020 at 09:25:51. This file was assigned entry number 93893 in the MFT.
After waiting 10 seconds, a second file was created with the long name
'4096_512_15_Seconds02', in the same folder, at 09:26:01.
After waiting
300 seconds, the file was deleted with the name '4096_512_15_Seconds01' and,
after a wait of 15000 milliseconds, the file '4096_512_15_Seconds02' was
renamed to '4096_512_15_Seconds01'.
As you can see
from the above table extracts, the file '4096_512_15_Seconds01', which occupied
the entry number 93893 in the MFT, has been deleted and, the file
'4096_512_15_Seconds02', which occupies the entry 94000 in the MFT, has now
been renamed '4096_512_15_Seconds01'.
With regard to
the time stamps, in both cases the original dates are shown for each of the two
files, so, with a waiting time of 15000 milliseconds, no tunnel effect has been
generated.
CCRR
Create a file 'A' in a folder; create a file 'B', in
the same folder; rename file 'A' as 'C'; and rename file 'B' as 'A
- Create a 512-byte 'A' file with a long name
- Create a 512-byte 'B' file with a long name
- Rename the file 'A' as 'C
- Set a timeout of 14000 milliseconds
- Rename file 'B' to 'A
In this test, as
you can see in the previous animated image, a file with the long name
'512-14-LFN01' was created in the system in the 'Test' folder, on 29-05-2020 at
15:54:55. This file was assigned the entry number 93893 in the MFT. After
waiting 10 seconds, a second file was created with the long name
'512-14-LFN02', in the same folder, at 15:55:06. This second file was assigned
entry number 93995 in the MFT.
After waiting
300 seconds, the file was renamed '512-14-LFN01' to '512-14-LFN03' and, after a
wait of 14000 milliseconds, the file was renamed '512-14-LFN02' to
'512-14-LFN01'.
As you can see
from the above table extracts, the file '512-14-LFN01', which occupies the
entry number 93893 in the MFT, has been renamed and still occupies the same
entry and, the file '512-14-LFN02', which occupies the entry 93995 in the MFT,
has now been renamed '512-14-LFN01'.
As far as time
stamps are concerned, the file renamed from '512-14-LFN02' to '512-14-LFN01'
was created on 29-05-2020 at 15:55:06, (in green). However, as you can see,
when you rename it with the same file name as the one previously renamed to
'512-14-LFN03', it acquires the creation date of that renamed file, at
15:54:55, (in red), showing, in the other timestamps, the original creation
date of the file. This indicates that, in this case, with a waiting time of
14000 milliseconds, a tunnel effect has been generated.
Create a file 'A' in a folder; create a file 'B', in
the same folder; rename file 'A' as 'C'; and rename file 'B' as 'A
- Create a 512-byte 'A' file with a long name
- Create a 512-byte 'B' file with a long name
- Rename the file 'A' as 'C
- Set a timeout of 15000 milliseconds
- Rename file 'B' to 'A
In this test, as
you can see in the previous animated image, a file with the long name
'512-15-LFN01' was created in the system in the 'Test' folder, on 01-06-2020 at
10:32:25. This file was assigned the entry number 93893 in the MFT. After
waiting 10 seconds, a second file was created with the long name
'512-15-LFN02', in the same folder, at 10:32:36. This second file was assigned
entry number 94000 in the MFT.
After waiting
300 seconds, the file was renamed '512-15-LFN01' to '512-15-LFN03' and, after a
wait of 15000 milliseconds, the file was renamed '512-15-LFN02' to
'512-15-LFN01'.
As you can see
from the above table extracts, the file '512-15-LFN01', which occupies the
entry number 93893 in the MFT, has been renamed and still occupies the same
entry and, the file '512-15-LFN02', which occupies the entry 94000 in the MFT,
has now been renamed '512-15-LFN01'.
As far as time
stamps are concerned, in both cases the original dates are shown for each of
the two files, so, with a timeout of 15000 milliseconds, no tunnel effect has
been generated.
Create a file 'A' in a folder; create a file 'B', in
the same folder; rename file 'A' as 'C'; and rename file 'B' as 'A
- Create a 512-byte 'A' file with a long name
- Create a 512-byte 'B' file with a short name
- Rename the file 'A' as 'C
- Set a timeout of 14000 milliseconds
- Rename file 'B' to 'A
In this test, as
you can see in the previous animated image, a file with the long name
'512-14-LFN01' was created in the system in the 'Test' folder, on 30-05-2020 at
15:13:13. This file was assigned the entry number 93893 in the MFT. After
waiting for 10 seconds, a second file with the short name '512-14~2', which is
the equivalent of a short name 8.3, was created in the same folder at 15:13:23.
This second file was assigned the entry number 93996 in the MFT.
After waiting
300 seconds, the file was renamed '512-14-LFN01' to '512-14-LFN03' and after a
wait of 14000 milliseconds, the file was renamed '512-14~2' to '512-14-LFN01'.
As you can see
from the above table extracts, the file '512-14-LFN01', which occupies the
entry number 93893 in the MFT, has been renamed and still occupies the same
entry and, the file '512-14~2', which occupies the entry 93996 in the MFT, has
now been renamed '512-14-LFN01'.
Regarding time
stamps, the file renamed from '512-14~2' to '512-14-LFN01' was created on
30-05-2020 at 15:13:23, (in green). However, as you can see, when you rename it
with the same file name as the one renamed before to '512-14-LFN03', it
acquires the creation date of that renamed file, at 15:13:13, (in red),
showing, in the other timestamps, the original creation date of the file. This
indicates that, in this case, with a waiting time of 14000 milliseconds, a
tunnel effect has been generated.
Create a file 'A' in a folder; create a file 'B', in
the same folder; rename file 'A' as 'C'; and rename file 'B' as 'A
- Create a 512-byte 'A' file with a long name
- Create a 512-byte 'B' file with a short name
- Rename the file 'A' as 'C
- Set a timeout of 15000 milliseconds
- Rename file 'B' to 'A
In this test, as
you can see in the previous animated image, a file with the long name
'512-15-LFN01' was created in the system in the 'Test' folder, on 02-06-2020 at
09:56:02. This file was assigned the entry number 93893 in the MFT. After
waiting for 10 seconds, a second file with the short name '512-15~2', which is
the equivalent of a short name 8.3, was created in the same folder at 09:56:11.
This second file was assigned the entry number 94001 in the MFT.
After waiting
for 300 seconds, the file was renamed '512-15-LFN01' to '512-15-LFN03' and
after a wait of 15000 milliseconds, the file was renamed '512-15~2' to
'512-15-LFN01'.
As you can see
from the above table extracts, the file '512-15-LFN01', which occupies the
entry number 93893 in the MFT, has been renamed and still occupies the same
entry and, the file '512-15~2', which occupies the entry 94000 in the MFT, has
now been renamed '512-15-LFN01'.
As far as time
stamps are concerned, in both cases the original dates are shown for each of
the two files, so with a timeout of 15000 milliseconds, no tunnel effect has
been generated.
Create a file 'A' in a folder; create a file 'B', in
the same folder; rename file 'A' as 'C'; and rename file 'B' as 'A
- Create a 512-byte 'A' file with a short name
- Create a 512-byte 'B' file with a short name
- Rename the file 'A' as 'C
- Set a timeout of 14000 milliseconds
- Rename file 'B' to 'A
In this test, as
you can see in the previous animated image, a file with the short name
'512-14~1' was created in the system in the 'Test' folder, on 01-06-2020 at
05:35:48. This file was assigned the entry number 93893 in the MFT. After
waiting for 10 seconds, a second file with the short name '512-14~2' was created
in the same folder at 05:35:58. This second file was assigned the entry number
94000 in the MFT.
After waiting
300 seconds, the file was renamed '512-14~1' to '512-14~3' and after a wait of
14000 milliseconds, the file was renamed '512-14~2' to '512-14~1'.
As you can see
from the above table extracts, the file '512-14~1', which occupies the entry
number 93893 in the MFT, has been renamed and still occupies the same entry
and, the file '512-14~2', which occupies the entry 94000 in the MFT, has now been
renamed '512-14~1'.
As far as
timestamps are concerned, the file renamed from '512-14~2' to '512-14~1' was
created on 01-06-2020 at 05:35:58, (in green). However, as you can see, when
you rename it with the same file name as the one renamed before to '512-14~3',
it acquires the creation date of that renamed file, at 05:35:48, (in red),
showing, in the other timestamps, the original creation date of the file. This
indicates that, in this case, with a waiting time of 14000 milliseconds, a
tunnel effect has been generated.
Create a file 'A' in a folder; create a file 'B', in
the same folder; rename file 'A' as 'C'; and rename file 'B' as 'A
- Create a 512-byte 'A' file with a short name
- Create a 512-byte 'B' file with a short name
- Rename the file 'A' as 'C
- Set a timeout of 15000 milliseconds
- Rename file 'B' to 'A
In this test, as
you can see in the previous animated image, a file with the long name
'512-14~1' was created in the system in the 'Test' folder, on 02-06-2020 at
10:27:39. This file was assigned the entry number 93893 in the MFT. After
waiting for 10 seconds, a second file with the short name '512-14~2' was
created in the same folder at 10:27:49.
After waiting
for 300 seconds, the file was renamed '512-15~1' to '512-15~3' and after a wait
of 15000 milliseconds, the file was renamed '512-15~2' to '512-15~1'.
As you can see
from the above table extracts, the file '512-15~1', which occupies the entry
number 93893 in the MFT, has been renamed and still occupies the same entry
and, the file '512-15~2', which occupies the entry 94002 in the MFT, has now
been renamed '512-15~1'.
As far as time
stamps are concerned, in both cases the original dates are shown for each of
the two files, so with a waiting time of 15000 milliseconds, no tunnel effect
has been generated.
Create a file 'A' in a folder; create a file 'B', in
the same folder; rename file 'A' as 'C'; and rename file 'B' as 'A
- Create a 512-byte 'A' file with a long name
- Create a 4096 byte 'B' file with a long name
- Rename the file 'A' as 'C
- Set a timeout of 14000 milliseconds
- Rename file 'B' to 'A
In this test, as
you can see in the previous animated image, a file with the long name
'512-14-LFN01' was created in the system in the 'Test' folder, on 31-05-2020 at
14:29:32. This file was assigned the entry number 93893 in the MFT. After
waiting 10 seconds, a second file was created with the long name
'512-14-LFN02', in the same folder, at 14:29:42. This second file was assigned
entry number 94000 in the MFT.
After waiting
300 seconds, the file was renamed '512-14-LFN01' to '512-14-LFN03' and, after a
wait of 14000 milliseconds, the file was renamed '512-14-LFN02' to
'512-14-LFN01'.
As you can see
from the above table extracts, the file '512-14-LFN01', which occupies the
entry number 93893 in the MFT, has been renamed and still occupies the same
entry and, the file '512-14-LFN02', which occupies the entry 94000 in the MFT,
has now been renamed '512-14-LFN01'.
Regarding time
stamps, the file renamed from '512-14-LFN02' to '512-14-LFN01' was created on
31-05-2020 at 14:29:42, (in green). However, as you can see, when you rename it
with the same file name as the one previously renamed to '512-14-LFN03', it
acquires the creation date of that renamed file, at 14:29:32, (in red),
showing, in the other timestamps, the original creation date of the file. This
indicates that, in this case, with a waiting time of 14000 milliseconds, a
tunnel effect has been generated.
Create a file 'A' in a folder; create a file 'B', in
the same folder; rename file 'A' as 'C'; and rename file 'B' as 'A
- Create a 512-byte 'A' file with a long name
- Create a 4096 byte 'B' file with a long name
- Rename the file 'A' as 'C
- Set a timeout of 15000 milliseconds
- Rename file 'B' to 'A
In this test, as
you can see in the previous animated image, a file with the long name
'512-15-LFN01' was created in the system in the 'Test' folder, on 02-06-2020 at
10:05:54. This file was assigned the entry number 93893 in the MFT. After
waiting 10 seconds, a second file with the long name '512-15-LFN02' was created
in the same folder at 10:06:04. This second file was assigned entry number
94000 in the MFT.
After waiting
300 seconds, the file was renamed '512-15-LFN01' to '512-15-LFN03' and, after a
wait of 15000 milliseconds, the file was renamed '512-15-LFN02' to
'512-15-LFN01'.
As you can see
from the above table extracts, the file '512-15-LFN01', which occupies the
entry number 93893 in the MFT, has been renamed and still occupies the same
entry and, the file '512-15-LFN02', which occupies the entry 94000 in the MFT,
has now been renamed '512-15-LFN01'.
As far as time
stamps are concerned, in both cases the original dates are shown for each of
the two files, so, with a timeout of 15000 milliseconds, no tunnel effect has
been generated.
Create a file 'A' in a folder; create a file 'B', in
the same folder; rename file 'A' as 'C'; and rename file 'B' as 'A
- Create a 4096 byte 'A' file with a long name
- Create a 512-byte 'B' file with a long name
- Rename the file 'A' as 'C
- Set a timeout of 14000 milliseconds
- Rename file 'B' to 'A
In this test, as
you can see in the previous animated image, a file with the long name
'512-14-LFN01' was created in the system in the 'Test' folder, on 02-06-2020 at
11:21:07. This file was assigned the entry number 93893 in the MFT. After
waiting 10 seconds, a second file with the long name '512-14-LFN02' was created
in the same folder at 11:21:17. This second file was assigned entry number
94000 in the MFT.
After waiting
300 seconds, the file was renamed '512-14-LFN01' to '512-14-LFN03' and, after a
wait of 14000 milliseconds, the file was renamed '512-14-LFN02' to
'512-14-LFN01'.
As you can see
from the above table extracts, the file '512-14-LFN01', which occupies the
entry number 93893 in the MFT, has been renamed and still occupies the same
entry and, the file '512-14-LFN02', which occupies the entry 94000 in the MFT,
has now been renamed '512-14-LFN01'.
Regarding time
stamps, the file renamed from '512-14-LFN02' to '512-14-LFN01' was created on
02-06-2020 at 11:21:17, (in green). However, as you can see, when you rename it
with the same file name as the one previously renamed to '512-14-LFN03', it
acquires the creation date of that renamed file, at 11:21:07, (in red),
showing, in the other timestamps, the original creation date of the file. This
indicates that, in this case, with a waiting time of 14000 milliseconds, a
tunnel effect has been generated.
Create a file 'A' in a folder; create a file 'B', in
the same folder; rename file 'A' as 'C'; and rename file 'B' as 'A
- Create a 4096 byte 'A' file with a long name
- Create a 512-byte 'B' file with a long name
- Rename the file 'A' as 'C
- Set a timeout of 15000 milliseconds
- Rename file 'B' to 'A
In this test, as
you can see in the previous animated image, a file with the long name
'512-15-LFN01' was created in the system in the 'Test' folder, on 02-06-2020 at
11:29:49. This file was assigned the entry number 93893 in the MFT. After
waiting 10 seconds, a second file was created with the long name
'512-15-LFN02', in the same folder, at 11:29:59. This second file was assigned
entry number 94000 in the MFT.
After waiting
300 seconds, the file was renamed '512-15-LFN01' to '512-15-LFN03' and, after a
wait of 15000 milliseconds, the file was renamed '512-15-LFN02' to
'512-15-LFN01'.
As you can see
from the above table extracts, the file '512-15-LFN01', which occupies the
entry number 93893 in the MFT, has been renamed and still occupies the same
entry and, the file '512-15-LFN02', which occupies the entry 94000 in the MFT,
has now been renamed '512-15-LFN01'.
As far as time
stamps are concerned, in both cases the original dates are shown for each of
the two files, so, with a timeout of 15000 milliseconds, no tunnel effect has
been generated.
CDC
Create an 'A' file in a folder; delete the 'A' file;
and recreate an 'A' file in the same folder
- Create a 512-byte 'A' file with a long name
- Delete the 'A' file
- Set a timeout of 14000 milliseconds
- Re-create a 512-byte 'A' file with a long name in
the same folder
In this test, as
you can see in the previous animated image, a file with the long name
'512-14-LFN' was created in the system in the 'Test' folder, on 29-05-2020 at
17:27:12. This file was assigned the entry number 93893 in the MFT.
After waiting
300 seconds, the file with the name '512-14-LFN' was deleted and, after a wait
of 14000 milliseconds, another file of the same size was created again, in the
same folder, with the name '512-14-LFN'.
As you can see
from the above table extracts, the file '512-14-LFN', which occupied the entry
number 93893 in the MFT, has been deleted. Similarly, the file '512-14-LFN',
which occupies the entry 93011 in the MFT, has been created.
As far as the
timestamps are concerned, the last file created, which occupies the entry
number 93011, was created on 29-05-2020 at 17:32:26. However, as you can see,
when it is created with the same file name as the previously deleted one, it
acquires the creation date of that deleted file, at 17:27:12, (in red),
showing, in the other timestamps, the original creation date of the file. This
indicates that, in this case, with a waiting time of 14000 milliseconds, a
tunnel effect has been generated.
Create an 'A' file in a folder; delete the 'A' file;
and recreate an 'A' file in the same folder
- Create a 512-byte 'A' file with a long name
- Delete the 'A' file
- Set a timeout of 15000 milliseconds
In this test, as
you can see in the previous animated image, a file with the long name
'512-15-LFN' was created in the system in the 'Test' folder, on 01-06-2020 at
15:51:03. This file was assigned the entry number 93893 in the MFT.
After waiting
300 seconds, the file named '512-15-LFN' was deleted and, after a wait of 15000
milliseconds, another file of the same size was created again, in the same
folder, with the name '512-15-LFN'.
As you can see
from the table extracts above, the file '512-15-LFN', which occupied the entry
number 93893 in the MFT, has been deleted and is no longer available in the
MFT, as that entry has been replaced by another one that now belongs to the
file 'ht_settings.ini', in the Active Disk Editor application, at 15:57:26. In
the same way, the file '512-15-LFN' has been created, which occupies the entry
93751 in the MFT.
As far as time
stamps are concerned, the original dates for the newly created file are shown,
so with a timeout of 15000 milliseconds, no tunnel effect has been generated.
Create an 'A' file in a folder; delete the 'A' file;
and recreate an 'A' file in the same folder
- Create a 512-byte 'A' file with a long name
- Delete the 'A' file
- Set a timeout of 14000 milliseconds
- Re-create a 512-byte 'A' file with a short name in
the same folder
In this test, as
you can see in the previous animated image, a file with the long name
'512-14-LFN' was created in the system in the 'Test' folder, on 31-05-2020 at
05:27:08. This file was assigned the entry number 93893 in the MFT.
After waiting
for 300 seconds, the file with the name '512-14-LFN' was deleted and, after a
wait of 14000 milliseconds, another file of the same size was created again, in
the same folder, with the short name '512-14~1'.
As you can see
in the previous table extracts, the file '512-14-LFN', which occupied the entry
number 93893 in the MFT, has been removed and is no longer available in the
MFT, as that entry has been replaced by another one that now belongs to the
file 'ht_settings.ini', from the Active Disk Editor application, at 15:57:26.
Similarly, the file '512-14~1' has been created, which occupies the entry 93751
in the MFT.
As far as time
stamps are concerned, the original dates for the newly created file are shown,
so with a timeout of 14000 milliseconds, no tunnel effect has been generated.
Create an 'A' file in a folder; delete the 'A' file;
and recreate an 'A' file in the same folder
- Create a 512-byte 'A' file with a short name
- Delete the 'A' file
- Set a timeout of 14000 milliseconds
- Re-create a 512-byte 'A' file with a short name in
the same folder
In this test, as
you can see in the previous animated image, a file with the short name
'512-14~1' was created in the system in the 'Test' folder, on 01-06-2020 at
05:45:26. This file was assigned the entry number 93893 in the MFT.
After waiting
300 seconds, the file with the name '512-14~1' was deleted and after a wait of
14000 milliseconds, another file of the same size was created again, in the
same folder, with the short name '512-14~1'.
As you can see
from the table extracts above, the file '512-14~1', which occupied the entry
number 93893 in the MFT, has been deleted and is no longer available in the
MFT, as that entry has been replaced by another one that now belongs to the
file 'ht_settings.ini', from the Active Disk Editor application, at 05:51:30.
Similarly, the file '512-14~1' has been created, which occupies the entry 93750
in the MFT.
As far as time
stamps are concerned, the last file created, which occupies entry number 93750,
was created on 01-06-2020 at 05:50:40. However, as you can see, when it is
created with the same file name as the previously deleted one, it acquires the
creation date of that deleted file, at 05:45:26, (in red), showing, in the
other time stamps, the original creation date of the file. This indicates that,
in this case, with a waiting time of 14000 milliseconds, a tunnel effect has
been generated.
Create an 'A' file in a folder; delete the 'A' file;
and recreate an 'A' file in the same folder
- Create a 512-byte 'A' file with a short name
- Delete the 'A' file
- Set a timeout of 15000 milliseconds
- Re-create a 512-byte 'A' file with a short name in
the same folder
In this test, as you can see in the previous
animated image, a file with the short name '512-15~1' was created in the system
in the 'Test' folder, on 02-06-2020 at 16:00:10. This file was assigned the
entry number 93893 in the MFT.
After waiting
300 seconds, the file with the name '512-15~1' was deleted, and after a wait of
15000 milliseconds, another file of the same size was created again, in the
same folder, with the short name '512-15~1'.
As you can see
from the table extracts above, the file '512-15~1', which occupied the entry
number 93893 in the MFT, has been deleted and is no longer available in the
MFT, as that entry has been replaced by another one that now belongs to the
file 'ht_settings.ini', in the Active Disk Editor application, at 16:06:20.
Similarly, the file '512-15~1' has been created, which occupies the entry 93011
in the MFT.
As far as time
stamps are concerned, the original dates for the newly created file are shown,
so with a timeout of 15000 milliseconds, no tunnel effect has been generated.
Create an 'A' file in a folder; delete the 'A' file;
and recreate an 'A' file in the same folder
- Create a 512-byte 'A' file with a long name
- Delete the 'A' file
- Set a timeout of 14000 milliseconds
- Re-create a 4096 byte 'A' file with a long name in
the same folder
In this test, as
you can see in the previous animated image, a file with the long name
'512_4096_14_Seconds' was created in the system in the 'Test' folder, on
31-05-2020 at 14:39:16. This file was assigned the entry number 93893 in the
MFT.
After waiting
300 seconds, the file with the name '512_4096_14_Seconds' was deleted and,
after a wait of 14000 milliseconds, another file of the same size was created
again, in the same folder, with the name '512_4096_14_Seconds'.
As you can see
from the table extracts above, the file '512_4096_14_Seconds', which occupied
the entry number 93893 in the MFT, has been deleted. Similarly, the file
'512_4096_14_Seconds' has been created, which occupies the entry 92614 in the
MFT.
As far as time
stamps are concerned, the last file created, which occupies entry number 92614,
was created on 31-05-2020 at 14:44:30. However, as you can see, by creating it
with the same file name as the previously deleted one, it acquires the creation
date of that deleted file, at 14:39:16, (in red), showing, in the other
timestamps, the original creation date of the file. This indicates that, in
this case, with a waiting time of 14000 milliseconds, a tunnel effect has been
generated.
Create an 'A' file in a folder; delete the 'A' file;
and recreate an 'A' file in the same folder
- Create a 512-byte 'A' file with a long name
- Delete the 'A' file
- Set a timeout of 15000 milliseconds
- Re-create a 4096 byte 'A' file with a long name in
the same folder
In this test, as
you can see in the previous animated image, a file with the long name
'512_4096_15_Seconds' was created in the system in the 'Test' folder, on
02-06-2020 at 15:50:46.
After waiting
300 seconds, the file with the name '512_4096_15_Seconds' was deleted and,
after a wait of 15000 milliseconds, another file of the same size was created
again, in the same folder, with the name '512_4096_15_Seconds'.
As you can see
from the table extracts above, the file '512_4096_15_Seconds', which occupied
the entry number 93893 in the MFT, has been removed and is no longer available
in the MFT, as that entry has been replaced by another one that now belongs to
the file 'ht_settings.ini', from the Active Disk Editor application, at 15:57:04.
Similarly, the file '512_4096_15_Seconds' has been created, which occupies the
entry 93751 in the MFT.
As far as time
stamps are concerned, the original dates for the newly created file are shown,
so, with a timeout of 15000 milliseconds, no tunnel effect has been generated.
Create an 'A' file in a folder; delete the 'A' file;
and recreate an 'A' file in the same folder
- Create a 4096 byte 'A' file with a long name
- Delete the 'A' file
- Set a timeout of 14000 milliseconds
- Re-create a 512-byte 'A' file with a long name in
the same folder
In this test, as
you can see in the previous animated image, a file with the long name
'4096_512_14_Seconds' was created in the system in the 'Test' folder, on
02-06-2020 at 16:08:23. This file was assigned entry number
93893 in the MFT.
After waiting
300 seconds, the file with the name '4096_512_14_Seconds' was deleted and,
after a wait of 14000 milliseconds, another file of the same size was created
again, in the same folder, with the name '4096_512_14_Seconds'.
As you can see
from the table extracts above, the file '4096_512_14_Seconds', which occupied
the entry number 93893 in the MFT, has been removed and is no longer available
in the MFT, as that entry has been replaced by another one that now belongs to
the file 'ht_settings.ini', from the Active Disk Editor application, at
16:14:48. In the same way, the file '4096_512_14_Seconds' has been created,
which occupies the entry 93750 in the MFT.
Regarding the
timestamps, the last file created, which occupies the entry number 93750, was
created on 02-06-2020 at 16:13:37. However, as you can see, when it is created
with the same file name as the previously deleted one, it acquires the creation
date of that deleted file, at 16:08:23, (in red), showing, in the other
timestamps, the original creation date of the file. This indicates that, in
this case, with a waiting time of 14000 milliseconds, a tunnel effect has been
generated.
Create an 'A' file in a folder; delete the 'A' file;
and recreate an 'A' file in the same folder
- Create a 4096 byte 'A' file with a long name
- Delete the 'A' file
- Set a timeout of 15000 milliseconds
- Re-create a 512-byte 'A' file with a long name in
the same folder
In this test, as
you can see in the previous animated image, a file with the long name
'4096_512_15_Seconds' was created in the system in the 'Test' folder, on
02-06-2020 at 16:16:20. This file was assigned entry number
93893 in the MFT.
After waiting
300 seconds, the file with the name '4096_512_15_Seconds' was deleted and,
after a wait of 15000 milliseconds, another file of the same size was created
again, in the same folder, with the name '4096_512_15_Seconds'.
As you can see
from the table extracts above, the file '4096_512_15_Seconds', which occupied
the entry number 93893 in the MFT, has been removed and is no longer available
in the MFT, as that entry has been replaced by another one that now belongs to
the file 'ht_settings.ini', from the Active Disk Editor application, at
16:22:32. In the same way, the file '4096_512_15_Seconds' has been created,
which occupies the entry 93751 in the MFT.
As far as time
stamps are concerned, the original dates for the newly created file are shown,
so, with a waiting time of 15000 milliseconds, no tunnel effect has been
generated.
CMC
Create an 'A' file in a folder; move the 'A' file to
another folder; and recreate an 'A' file, in the same original folder
- Create a 512-byte 'A' file with a long name
- Move file 'A' to another folder
- Set a timeout of 14000 milliseconds
- Re-create a 512-byte 'A' file with a long name in
the same original creation folder
In this test, as
you can see in the previous animated image, a file with the long name
'512-14-LFN' was created in the system in the 'Test' folder, on 30-05-2020 at
06:41:18. This file was assigned the entry number 93893 in the MFT.
After waiting
300 seconds, the file named '512-14-LFN' was moved to the 'Moved' folder and,
after a wait of 14000 milliseconds, another file of the same size was created
again, in the same folder, with the name '512-14-LFN'.
As you can see
from the above table extracts, the file '512-14-LFN', which occupied the entry
number 93893 in the MFT, has been moved. Similarly, the file '512-14-LFN',
which occupies the entry 93011 in the MFT, has been created.
Regarding the
time stamps, the last file created, which occupies the entry number 93011, was
created on 30-05-2020 at 06:46:33. However, as you can see, when creating it
with the same file name as the previously moved, it acquires the creation date
of that moved file, at 06:41:18, (in red), presenting, in the other time stamps,
the original date of creation of the file. This indicates that, in this case,
with a waiting time of 14000 milliseconds, a tunnel effect has been generated.
Create an 'A' file in a folder; move the 'A' file to
another folder; and recreate an 'A' file, in the same original folder
- Create a 512-byte 'A' file with a long name
- Move file 'A' to another folder
- Set a timeout of 15000 milliseconds
- Re-create a 512-byte 'A' file with a long name in
the same original creation folder
In this test, as
you can see in the previous animated image, a file with the long name
'512-15-LFN' was created in the system in the 'Test' folder, on 01-06-2020 at
10:53:41. This file was assigned the entry number 93893 in the MFT.
After waiting
300 seconds, the file named '512-15-LFN' was moved to the 'Moved' folder and,
after a wait of 15000 milliseconds, another file of the same size was created
again, in the same folder, with the name '512-15-LFN'.
As you can see
from the above table extracts, the file '512-15-LFN', which occupied the entry
number 93893 in the MFT, has been moved. Similarly, the file '512-15-LFN',
which occupies the entry 92614 in the MFT, has been created.
As far as time
stamps are concerned, the original dates for the newly created file are shown,
so, with a waiting time of 15000 milliseconds, no tunnel effect has been
generated.
Create an 'A' file in a folder; move the 'A' file to
another folder; and recreate an 'A' file, in the same original folder
- Create a 512-byte 'A' file with a long name
- Move file 'A' to another folder
- Set a timeout of 14000 milliseconds
- Re-create a 512-byte 'A' file with a short name in
the same folder where it was originally created
In this test, as
you can see in the previous animated image, a file with the long name
'512-14-LFN' was created in the system in the 'Test' folder, on 31-05-2020 at
05:35:37. This file was assigned the entry number 93893 in the MFT.
After waiting
for 300 seconds, the file named '512-14-LFN' was moved to the 'Moved' folder
and, after waiting for 14000 milliseconds, another file of the same size was
created again, in the same folder, with the short name '512-14~1'.
As you can see
from the above table extracts, the file '512-14-LFN', which occupied the entry
number 93893 in the MFT, has been moved. Similarly, the file '512-14~1', which
occupies the entry 93751 in the MFT, has been created.
As far as time
stamps are concerned, the original dates for the newly created file are shown,
so, with a waiting time of 14000 milliseconds, no tunnel effect has been
generated.
Create an 'A' file in a folder; move the 'A' file to
another folder; and recreate an 'A' file, in the same original folder
- Create a 512-byte 'A' file with a long name
- Move file 'A' to another folder
- Set a timeout of 14000 milliseconds
- Re-create a 512-byte 'A' file with a short name in
the same folder where it was originally created
In this test, as
you can see in the previous animated image, a file with the short name
'512-14~1' was created in the system in the 'Test' folder, on 01-06-2020 at
05:53:16. This file was assigned the entry number 93893 in the MFT.
After waiting
for 300 seconds, the file named '512-14~1' was moved to the 'Moved' folder and,
after waiting for 14000 milliseconds, another file of the same size was created
again, in the same folder, with the short name '512-14~1'.
As you can see
from the above table extracts, the file '512-14~1', which occupied the entry
number 93893 in the MFT, has been moved. Similarly, the file '512-14~1', which
occupies the entry 93751 in the MFT, has been created.
Regarding the
time stamps, the last file created, which occupies the entry number 93751, was
created on 01-06-2020 at 05:58:30. However, as you can see, by creating it with
the same file name as the previous one, it acquires the creation date of that
moved file, at 05:53:16, (in red), showing, in the other time stamps, the
original creation date of the file. This indicates that, in this case, with a
waiting time of 14000 milliseconds, a tunnel effect has been generated.
Create an 'A' file in a folder; move the 'A' file to
another folder; and recreate an 'A' file, in the same original folder
- Create a 512-byte 'A' file with a short name
- Move file 'A' to another folder
- Set a timeout of 15000 milliseconds
- Re-create a 512-byte 'A' file with a short name in
the same folder where it was originally created
In this test, as
you can see in the previous animated image, a file with the short name
'512-15~1' was created in the system in the 'Test' folder, on 02-06-2020 at
16:52:09. This file was assigned the entry number 93893 in the MFT.
After waiting
for 300 seconds, the file named '512-15~1' was moved to the 'Moved' folder, and
after a wait of 15000 milliseconds, another file of the same size was created
again, in the same folder, with the short name '512-15~1'.
As you can see
from the above table extracts, the file '512-15~1', which occupied the entry
number 93893 in the MFT, has been moved. Similarly, the file '512-15~1', which
occupies the entry 93750 in the MFT, has been created.
As far as time
stamps are concerned, the original dates for the newly created file are shown,
so, with a waiting time of 15000 milliseconds, no tunnel effect has been
generated.
Create an 'A' file in a folder; move the 'A' file to
another folder; and recreate an 'A' file, in the same original folder
- Create a 512-byte 'A' file with a long name
- Move file 'A' to another folder
- Set a timeout of 14000 milliseconds
- Re-create a 4096 byte 'A' file with a long name in
the same original creation folder
In this test, as
you can see in the previous animated image, a file with the long name
'512_4096_14_Seconds' was created in the system in the 'Test' folder, on
31-05-2020 at 18:06:41. This file was assigned the entry number 93893 in the
MFT.
After waiting
300 seconds, the file with the name '512_4096_14_Seconds' was moved to the
'Moved' folder and, after a wait of 14000 milliseconds, another file of the
same size was created again, in the same folder, with the long name
'512_4096_14_Seconds'.
As you can see
from the table extracts above, the file '512_4096_14_Seconds', which occupied
the entry number 93893 in the MFT, has been moved. Similarly, the file
'512_4096_14_Seconds', which occupies entry 93750 in the MFT, has been created.
Regarding the time
stamps, the last file created, which occupies the entry number 93750, was
created on 31-05-2020 at 18:11:55. However, as you can see, when it is created
with the same file name as the previously moved, it acquires the creation date
of that moved file, at 18:06:41, (in red), showing, in the other time stamps,
the original date of creation of the file. This indicates that, in this case,
with a waiting time of 14000 milliseconds, a tunnel effect has been generated.
Create an 'A' file in a folder; move the 'A' file to
another folder; and recreate an 'A' file, in the same original folder
- Create a 512-byte 'A' file with a long name
- Move file 'A' to another folder
- Set a timeout of 15000 milliseconds
- Re-create a 4096 byte 'A' file with a long name in
the same original creation folder
In this test, as
you can see in the previous animated image, a file with the long name
'512_4096_15_Seconds' was created in the system in the 'Test' folder, on
02-06-2020 at 16:43:24. This file was assigned the entry number 93893 in the
MFT.
After waiting
300 seconds, the file with the name '512_4096_15_Seconds' was moved to the
'Moved' folder and, after a wait of 15000 milliseconds, another file of the
same size was created again, in the same folder, with the short name
'512_4096_15_Seconds'.
As you can see
from the table extracts above, the file '512_4096_15_Seconds', which occupied
the entry number 93893 in the MFT, has been moved. Similarly, the file
'512_4096_15_Seconds', which occupies the entry 93751 in the MFT, has been
created.
As far as time
stamps are concerned, the original dates for the newly created file are shown,
so, with a waiting time of 15000 milliseconds, no tunnel effect has been
generated.
Create an 'A' file in a folder; move the 'A' file to
another folder; and recreate an 'A' file, in the same original folder
- Create a 4096 byte 'A' file with a long name
- Move file 'A' to another folder
- Set a timeout of 14000 milliseconds
- Re-create a 512-byte 'A' file with a long name in
the same original creation folder
In this test, as
you can see in the previous animated image, a file with the long name
'4096_512_14_Seconds' was created in the system in the 'Test' folder, on
02-06-2020 at 17:00:12. This file was assigned entry number
93893 in the MFT.
After waiting
300 seconds, the file with the name '4096_512_14_Seconds' was moved to the
'Moved' folder and, after a wait of 14000 milliseconds, another file of the
same size was created again, in the same folder, with the long name
'4096_512_14_Seconds'.
As you can see
from the table extracts above, the file '4096_512_14_Seconds', which occupied
the entry number 93893 in the MFT, has been moved. Similarly, the file
'4096_512_14_Seconds', which occupies the entry 93751 in the MFT, has been
created.
Regarding the
time stamps, the last file created, which occupies the entry number 93751, was
created on 02-06-2020 at 17:05:26. However, as you can see, when it is created
with the same file name as the previously moved, it acquires the creation date
of that moved file, at 17:00:12, (in red), showing, in the other time stamps,
the original date of creation of the file. This indicates that, in this case,
with a waiting time of 14000 milliseconds, a tunnel effect has been generated.
Create an 'A' file in a folder; move the 'A' file to
another folder; and recreate an 'A' file, in the same original folder
- Create a 4096 byte 'A' file with a long name
- Move file 'A' to another folder
- Set a timeout of 15000 milliseconds
- Re-create a 512-byte 'A' file with a long name in
the same original creation folder
In this test, as
you can see in the previous animated image, a file with the long name
'4096_512_15_Seconds' was created in the system in the 'Test' folder, on
02-06-2020 at 17:09:15. This file was assigned the entry number 93893 in the
MFT.
After waiting
300 seconds, the file with the name '4096_512_15_Seconds' was moved to the
'Moved' folder and, after a wait of 15000 milliseconds, another file of the
same size was created again, in the same folder, with the short name
'4096_512_15_Seconds'.
As you can see
from the table extracts above, the file '4096_512_15_Seconds', which occupied
the entry number 93893 in the MFT, has been moved. Similarly, the file
'4096_512_15_Seconds', which occupies entry 93750 in the MFT, has been created.
As far as time stamps
are concerned, the original dates for the newly created file are shown, so,
with a waiting time of 15000 milliseconds, no tunnel effect has been generated.
CRC
Create an 'A' file in a folder; rename the 'A' file;
and create an 'A' file again, in the same original folder
- Create a 512-byte 'A' file with a long name
- rename the file 'A
- Set a timeout of 14000 milliseconds
- Re-create a 512-byte 'A' file with a long name in
the same original creation folder
In this test, as
you can see in the previous animated image, a file with the long name
'512-14-LFN' was created in the system in the 'Test' folder, on 30-05-2020 at
11:15:16. This file was assigned the entry number 93893 in the MFT.
After waiting
300 seconds, the file was renamed '512-14-LFN' and, after a wait of 14000
milliseconds, another file of the same size was created again, in the same
folder, with the name '512-14-LFN'.
As you can see
from the above table extracts, the file '512-14-LFN', which occupied the entry
number 93893 in the MFT, has been renamed to 'New_512-14-LFN'. Similarly, the file
'512-14-LFN', which occupies the entry 92614 in the MFT, has been created.
Regarding the
time stamps, the last file created, which occupies the entry number 92614, was
created on 30-05-2020 at 11:20:30. However, as you can see, when you create it
with the same file name that you renamed before, it acquires the creation date
of that renamed file, at 11:15:16, (in red), showing, in the other time stamps,
the original creation date of the file. This indicates that, in this case, with
a waiting time of 14000 milliseconds, a tunnel effect has been generated.
Create an 'A' file in a folder; rename the 'A' file;
and create an 'A' file again, in the same original folder
- Create a 512-byte 'A' file with a long name
- rename the file 'A
- Set a timeout of 15000 milliseconds
- Re-create a 512-byte 'A' file with a long name in
the same original creation folder
In this test, as
you can see in the previous animated image, a file with the long name
'512-15-LFN' was created in the system in the 'Test' folder, on 01-06-2020 at
11:03:37. This file was assigned the entry number 93893 in the MFT.
After waiting
300 seconds, the file was renamed '512-15-LFN' and, after a wait of 15000
milliseconds, another file of the same size was created again, in the same
folder, with the name '512-15-LFN'.
As you can see
from the above table extracts, the file '512-15-LFN', which occupied the entry
number 93893 in the MFT, has been renamed to 'New_512-15-LFN'. Similarly, the
file '512-15-LFN', which occupies the entry 92614 in the MFT, has been created.
As far as time
stamps are concerned, the original dates for the newly created file are shown,
so, with a timeout of 15000 milliseconds, no tunnel effect has been generated.
Create an 'A' file in a folder; rename the 'A' file;
and create an 'A' file again, in the same original folder
- Create a 512-byte 'A' file with a long name
- rename the file 'A
- Set a timeout of 14000 milliseconds
- Re-create a 512-byte 'A' file with a short name in
the same folder where it was originally created
In this test, as
you can see in the previous animated image, a file with the long name
'512-14-LFN' was created in the system in the 'Test' folder, on 31-05-2020 at
05:44:22. This file was assigned the entry number 93893 in the MFT.
After waiting
300 seconds, the file was renamed to '512-14-LFN' and after a wait of 14000
milliseconds, another file of the same size was created again, in the same
folder, with the name '512-14~1'.
As you can see
from the above table extracts, the file '512-15-LFN', which occupied the entry
number 93893 in the MFT, has been renamed to 'New_512-14-LFN'. Similarly, the
file '512-14~1' has been created, which occupies the entry 93750 in the MFT.
As far as time
stamps are concerned, the original dates for the newly created file are shown,
so with a timeout of 14000 milliseconds, no tunnel effect has been generated.
Create an 'A' file in a folder; rename the 'A' file;
and create an 'A' file again, in the same original folder
- Create a 512-byte 'A' file with a short name
- rename the file 'A
- Set a timeout of 14000 milliseconds
- Re-create a 512-byte 'A' file with a short name in
the same folder where it was originally created
In this test, as
you can see in the previous animated image, a file with the short name
'512-14~1' was created in the system in the 'Test' folder, on 01-06-2020 at
06:02:39. This file was assigned the entry number 93893 in the MFT.
After waiting
300 seconds, the file was renamed to '512-14~1' and, after a wait of 14000
milliseconds, another file of the same size was created again, in the same
folder, with the name '512-14~1'.
As you can see
from the above table extracts, the file '512-14~1', which occupied the entry
number 93893 in the MFT, has been renamed to 'N51214LFN'. Similarly, the file
'512-14~1', which occupies the entry 92614 in the MFT, has been created.
As far as the
timestamps are concerned, the last file created, which occupies the entry
number 92614, was created on 01-06-2020 at 06:07:53. However, as you can see,
when it is created with the same file name as the previously renamed one, it
acquires the creation date of that renamed file, at 06:02:39, (in red),
showing, in the other timestamps, the original creation date of the file. This
indicates that, in this case, with a waiting time of 14000 milliseconds, a
tunnel effect has been generated.
Create an 'A' file in a folder; rename the 'A' file;
and create an 'A' file again, in the same original folder
- Create a 512-byte 'A' file with a short name
- rename the file 'A
- Set a timeout of 15000 milliseconds
- Re-create a 512-byte 'A' file with a short name in
the same folder where it was originally created
In this test, as
you can see in the animation above, a file with the short name '512-15~1' was
created in the system in the 'Test' folder, on 04-06-2020 at 11:33:33. This
file was assigned the entry number 93893 in the MFT.
After waiting
300 seconds, the file was renamed to '512-15~1' and after a wait of 15000
milliseconds, another file of the same size was created again, in the same
folder, with the name '512-15~1'.
As you can see
from the above table extracts, the file '512-15~1', which occupied the entry
number 93893 in the MFT, has been renamed to 'N51215LFN'. Similarly, the file
'512-15~1', which occupies the entry 93750 in the MFT, has been created.
As far as time
stamps are concerned, the original dates for the newly created file are shown,
so with a timeout of 15000 milliseconds, no tunnel effect has been generated.
Create an 'A' file in a folder; rename the 'A' file;
and create an 'A' file again, in the same original folder
- Create a 512-byte 'A' file with a long name
- rename the file 'A
- Set a timeout of 14000 milliseconds
- Re-create a 4096 byte 'A' file with a long name in
the same original creation folder
In this test, as
you can see in the previous animated image, a file with the long name
'512_4096_14_Seconds' was created in the system in the 'Test' folder, on
31-05-2020 at 14:58:26. This file was assigned the entry number 93893 in the
MFT.
After waiting
300 seconds, the file was renamed '512_4096_14_Seconds' and, after a wait of
14000 milliseconds, another file of the same size was created again, in the same
folder, with the name '512_4096_14_Seconds'.
As you can see
from the above table extracts, the file '512_4096_14_Seconds', which occupied
the entry number 93893 in the MFT, has been renamed to
'New_512_4096_14_Seconds'. Similarly, the file '512_4096_14_Seconds' has been
created, which occupies the entry 92614 in the MFT.
As far as time
stamps are concerned, the last file created, which occupies entry number 92614,
was created on 31-05-2020 at 15:03:40. However, as you can see, when you create
it with the same file name that was renamed before, it acquires the creation
date of that renamed file, at 14:58:26, (in red), showing, in the other time
stamps, the original creation date of the file. This indicates that, in this
case, with a waiting time of 14000 milliseconds, a tunnel effect has been
generated.
Create an 'A' file in a folder; rename the 'A' file;
and create an 'A' file again, in the same original folder
- Create a 512-byte 'A' file with a long name
- rename the file 'A
- Set a timeout of 14000 milliseconds
- Re-create a 4096 byte 'A' file with a long name in
the same original creation folder
In this test, as
you can see in the previous animated image, a file with the long name
'512_4096_15_Seconds' was created in the system in the 'Test' folder, on
04-06-2020 at 10:25:28. This file was assigned the entry number 93893 in the
MFT.
After waiting
300 seconds, the file was renamed '512_4096_15_Seconds' and, after a wait of
15000 milliseconds, another file of the same size was created again, in the
same folder, with the name '512_4096_15_Seconds'.
As you can see
from the above table extracts, the file '512_4096_15_Seconds', which occupied
the entry number 93893 in the MFT, has been renamed to
'New_512_4096_15_Seconds'. Likewise, the file '512_4096_15_Seconds' has been
created, which occupies the entry 92614 in the MFT.
As far as time
stamps are concerned, the original dates for the newly created file are shown,
so, with a waiting time of 15000 milliseconds, no tunnel effect has been
generated.
Create an 'A' file in a folder; rename the 'A' file;
and create an 'A' file again, in the same original folder
- Create a 4096 byte 'A' file with a long name
- rename the file 'A
- Set a timeout of 14000 milliseconds
- Re-create a 512-byte 'A' file with a long name in
the same original creation folder
In this test, as
you can see in the previous animated image, a file with the long name
'4096_512_14_Seconds' was created in the system in the 'Test' folder, on 04-06-2020
at 17:39:51. This file was assigned the entry number 93893 in the MFT.
After waiting
300 seconds, the file was renamed '4096_512_14_Seconds' and, after a wait of
14000 milliseconds, another file of the same size was created again, in the
same folder, with the name '4096_512_14_Seconds'.
As you can see
from the table extracts above, the file '4096_512_14_Seconds', which occupied
the entry number 93893 in the MFT, has been renamed to
'New_4096_512_14_Seconds'. Similarly, the file '4096_512_14_Seconds' has been
created, which occupies entry 93750 in the MFT.
As far as time
stamps are concerned, the last file created, which occupies entry number 93750,
was created on 04-06-2020 at 17:45:05. However, as you can see, when you create
it with the same file name as the one previously renamed, it acquires the
creation date of that renamed file, at 17:39:51, (in red), showing, in the
other time stamps, the original creation date of the file. This indicates that,
in this case, with a waiting time of 14000 milliseconds, a tunnel effect has
been generated.
Create an 'A' file in a folder; rename the 'A' file;
and create an 'A' file again, in the same original folder
- Create a 4096 byte 'A' file with a long name
- rename the file 'A
- Set a timeout of 15000 milliseconds
- Re-create a 512-byte 'A' file with a long name in
the same original creation folder
In this test, as
you can see in the previous animated image, a file with the long name
'4096_512_15_Seconds' was created in the system in the 'Test' folder, on
03-06-2020 at 07:50:58. This file was assigned entry number
93893 in the MFT.
After waiting
300 seconds, the file was renamed '4096_512_15_Seconds' and, after a wait of
15000 milliseconds, another file of the same size was created again, in the
same folder, with the name '4096_512_15_Seconds'.
As you can see
from the above table extracts, the file '4096_512_15_Seconds', which occupied
the entry number 93893 in the MFT, has been renamed to
'New_4096_512_15_Seconds'. Similarly, the file '4096_512_15_Seconds' has been
created, which occupies entry 93750 in the MFT.
As far as time
stamps are concerned, the original dates for the newly created file are shown,
so, with a waiting time of 15000 milliseconds, no tunnel effect has been
generated.
Disabling File System Tunneling
As I said at the
beginning of the article, you can disable the file system tunneling. To do
this, add the key “HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\FileSystem\MaximumTunnelEntries”,
in the Windows Registry, set a value of
'0', and reboot the system so that the new configuration applies.
Once this
configuration is applied, if we now execute any of the actions seen before, we
will obtain as a result that in no case a tunnel effect is generated.
As an example,
I'll show a single test, with a timeout of 10,000 milliseconds, instead of the
14,000 seen so far.
CCRR
Create a file 'A' in a folder; create a file 'B', in
the same folder; rename file 'A' as 'C'; and rename file 'B' as 'A
- Create a 512-byte 'A' file with a long name
- Create a 512-byte 'B' file with a long name
- Rename the file 'A' as 'C
- Set a timeout of 10,000 milliseconds
- Rename file 'B' to 'A
In this test, as
you can see in the previous animated image, a file with the long name
'512-15-LFN01' was created in the system in the 'Test' folder, on 06-06-2020 at
15:28:08. This file was assigned the entry number 93893 in the MFT. After
waiting 10 seconds, a second file was created with the long name
'512-15-LFN02', in the same folder, at 15:28:18. This second file was assigned
entry number 94050 in the MFT.
After waiting
300 seconds, the file was renamed '512-15-LFN01' to '512-15-LFN03' and, after a
wait of 10,000 milliseconds, the file was renamed '512-15-LFN02' to
'512-15-LFN01'.
As you can see
from the above table extracts, the file '512-15-LFN01', which occupies the
entry number 93893 in the MFT, has been renamed and still occupies the same
entry and, the file '512-15-LFN02', which occupies the entry 94050 in the MFT,
has now been renamed '512-15-LFN01'.
As far as time
stamps are concerned, in both cases the original dates are shown for each of
the two files, so, with a waiting time of 10,000 milliseconds, no tunnel effect
has been generated.
Overwriting files, with file system tunneling disabled
While testing
with the file system tunneling disabled, I came across another unexpected test,
as I didn't have it in mind. It consists of overwriting a file with another
file of the same name. So, what I did was to execute a first tunneling test
and, once finished, to execute again the same test so that the generated file
was overwritten, in order to observe its behavior.
CDCC
Create an 'A' file in a folder; delete the 'A' file;
and recreate an 'A' file in the same folder
- Create a 512-byte 'A' file with a long name
- Delete the 'A' file
- Set a timeout of 14000 milliseconds
- Re-create a 512-byte 'A' file with a long name in
the same folder
- Re-create a 512-byte 'A' file with a long name in
the same folder, overwriting the previous one
In this test, as
you can see in the previous animated image, a file with the long name
'512-14-LFN' was created in the system in the 'Test' folder, on 06-06-2020 at
15:03:08. This file was assigned entry number 4203 in the MFT.
After waiting
300 seconds, the file with the name '512-14-LFN' was deleted and, after a wait
of 14000 milliseconds, another file of the same size was created again, in the
same folder, with the name '512-14-LFN'.
As you can see
from the above table extracts, the file '512-14-LFN', which occupied the entry
number 4203 in the MFT when the file was first created, still occupies the same
entry, with the same file name.
Regarding the
time stamps, the deleted file '512-14-LFN' was created on 06-06-2020 at
15:03:08, creating again a file with the same name '512-14-LFN', after a
waiting time of 14000 milliseconds, on 06-06-2020 at 15:08:18, presenting
correctly the time stamp of the creation of that file. This indicates that, in
this case, with a timeout of 14000 milliseconds, no tunnel effect has been
generated.
I create another
file with the same name of '512-14-LFN' to overwrite the existing one.
As you can see
in the extracts of the previous tables, the file '512-14-LFN' that has been generated
to overwrite the previous file, has in its creation date the day 06-06-2020 at
15:08:18, (in red), being, its correct creation date, the day 06-06-2020 at
15:11:26.
Setting a specific time in the file system tunneling
As I also said
at the beginning of the article, just as you can disable file system tunneling,
you can set a certain time in seconds for this tunneling effect to be
generated. To do this, you should add the key “HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\FileSystem\MaximumTunnelEntryAgeInSeconds”,
in the Windows Registry, set a numerical
value in seconds, and reboot the system so that the new configuration is
applied.
Once this
configuration is applied, if we now execute any of the actions seen before, we
will obtain as a result that a tunnel effect is generated within the
established time values.
As an example,
I'll show a single test below, with a timeout of 50,000 milliseconds, instead
of the 14,000 seen so far.
CCDR
Create a file 'A' in a folder; create a file 'B', in the
same folder; delete file 'A'; and rename file 'B' as 'A
- Create a 512-byte 'A' file with a long name
- Create a 512-byte 'B' file with a long name
- Delete the 'A' file
- Set a timeout of 50,000 milliseconds
- Rename file 'B' to 'A
In this test, as
you can see in the previous animated image, a file with the long name
'512-14-LFN01' was created in the system in the 'Test' folder, on 08-06-2020 at
08:25:39. This file was assigned the entry number 93893 in the MFT. After
waiting 10 seconds, a second file was created with the long name
'512-14-LFN02', in the same folder, at 08:25:48. This second file was assigned
entry number 94051 in the MFT.
After waiting
300 seconds, the file was deleted with the name '512-14-LFN01' and, after a wait
of 50000 milliseconds, the file was renamed '512-14-LFN02' to '512-14-LFN01'.
As you can see
from the above table extracts, the file '512-14-LFN01', which originally
occupied the entry number 93893, is no longer available in the MFT, as that
entry has been replaced by another one that now belongs to the file
'StartupProfileData-NonInteractive', by PowerShell, at 08:31:45. On the other
hand, the file '512-15-LFN02', which occupies the entry 94051 in the MFT, has
now been renamed '512-15-LFN01'.
Regarding
timestamps, the renamed file was created on 08-06-2020 at 08:25:48, (in green).
However, as you can see, by renaming it with the same file name as the deleted
one, it acquires the creation date of that deleted file, at 08:25:39, (in red),
showing, in the other timestamps, the original creation date of the file. This
indicates that, in this case, with a waiting time of 50000 milliseconds, a
tunnel effect has been generated.
Disabling the creation of short file names, (8.3)
It was said at
the beginning of this article that "The idea, (of file system tunneling)
is to imitate the behavior that MS-DOS programs expect when they use the secure
storage method.”
MS-DOS works
with short file names, (8.3). Thus, another way to disable file system
tunneling is to disable the creation of short file names on the system. To do
this, the value of the “HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\FileSystem\NtfsDisable8dot3NameCreation”
key in the Windows Registry must be changed to '1', and the system restarted to apply the new settings.
Once this
configuration is applied, if we now execute any of the actions seen before, we
will obtain as a result that in no case a tunnel effect is generated.
As an example,
I'll show two tests below, with long file names and short file names, and a
timeout of 14000 milliseconds.
CDC
Create an 'A' file in a folder; delete the 'A' file;
and recreate an 'A' file in the same folder
- Create a 512-byte 'A' file with a long name
- Delete the 'A' file
- Set a timeout of 14000 milliseconds
- Re-create a 512-byte 'A' file with a long name in
the same folder
In this test, as
you can see in the previous animated image, a file with the long name
'512-14-LFN' was created in the system in the 'Test' folder, on 18-06-2020 at
09:55:54. This file was assigned the entry number 93893 in the MFT.
After waiting
300 seconds, the file with the name '512-14-LFN' was deleted and, after a wait
of 14000 milliseconds, another file of the same size was created again, in the
same folder, with the name '512-14-LFN'.
As you can see
from the above table extracts, the file '512-14-LFN', which occupied the entry
number 93893 in the MFT when the file was first created, still occupies the
same entry, with the same file name.
Regarding the
time stamps, the deleted file '512-14-LFN' was created on 18-06-2020 at
09:55:54, creating again a file with the same name '512-14-LFN', after a
waiting time of 14000 milliseconds, on 18-06-2020 at 10:01:05, presenting
correctly the time stamp of the creation of that file. This indicates that, in
this case, with a waiting time of 14000 milliseconds, no tunnel effect has been
generated.
Create an 'A' file in a folder; delete the 'A' file;
and recreate an 'A' file in the same folder
- Create a 512-byte 'A' file with a short name
- Delete the 'A' file
- Set a timeout of 14000 milliseconds
- Re-create a 512-byte 'A' file with a short name in
the same folder
In this test, as
you can see in the previous animated image, a file with the short name
'512-15~1' was created in the system in the 'Test' folder, on 18-06-2020 at
10:16:00. This file was assigned the entry number 92610 in the MFT.
After waiting
300 seconds, the file with the name '512-15~1' was deleted, and after a wait of
14000 milliseconds, another file of the same size was created again, in the
same folder, with the short name '512-15~1'.
As you can see
from the above table extracts, the file '512-15~1', which occupied the entry
number 92610 in the MFT when the file was first created, still occupies the
same entry, with the same file name.
Regarding the
time stamps, the deleted file '512-15~1' was created on 18-06-2020 at 10:16:00,
creating again a file with the same name '512-15~1', after a waiting time of
14000 milliseconds, on 18-06-2020 at 10:21:14, presenting correctly the time
stamp of the creation of that file. This indicates that, in this case, with a
timeout of 14000 milliseconds, no tunnel effect has been generated.
Disabling last access update
If you're one of
those people who questions everything, (I do), you might be wondering if, by disabling
the timestamp update of the last access to a file. Let's look at it.
To do this, you
must change the value of the key “HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\FileSystem\NtfsDisableLastAccessUpdate”,
in the Windows Registry, setting this value to '1', and rebooting the system so that the new configuration is
applied.
Once this
configuration is applied, if we now execute any of the actions seen before, we
will obtain as a result that the tunnel effect continues to be generated in the
same way.
As an example,
I'll show a single test below, with a timeout of 14000 milliseconds.
CDC
Create an 'A' file in a folder; delete the 'A' file;
and recreate an 'A' file in the same folder
- Create a 512-byte 'A' file with a long name
- Delete the 'A' file
- Set a timeout of 14000 milliseconds
- Re-create a 512-byte 'A' file with a long name in
the same folder
In this test, as
you can see in the previous animated image, a file with the long name
'512-14-LFN' was created in the system in the 'Test' folder, on 18-06-2020 at
10:40:27. This file was assigned the entry number 93893 in the MFT.
After waiting
300 seconds, the file with the name '512-14-LFN' was deleted and, after a wait
of 14000 milliseconds, another file of the same size was created again, in the
same folder, with the name '512-14-LFN'.
As you can see
from the above table extracts, the file '512-14-LFN', which occupied the entry
number 93893 in the MFT, has been deleted. Similarly, the file '512-14-LFN',
which occupies the entry 90569 in the MFT, has been created.
Regarding the
timestamps, the last file created, which occupies the entry number 90569, was
created on 18-06-2020 at 10:45:41. However, as you can see, when created with
the same file name as the previously deleted, it acquires the creation date of
that deleted file, at 10:40:27, (in red), presenting, in the other timestamps,
the original date of creation of the file. This indicates that, in this case,
with a waiting time of 14000 milliseconds, a tunnel effect has been generated.
Determining a maximum tunneling value
Is there a
maximum value for file system tunneling and can it be calculated? It can, yes.
As with everything, it's a matter of time, and will.
To do this, I
have modified the value of the key “HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\FileSystem\MaximumTunnelEntryAgeInSeconds”,
in the Windows Registry, setting this value to '86400', (which is equivalent to one day converted to seconds),
and rebooting the system so that the new configuration is applied.
With this
configuration, I carried out the tests again, varying the waiting time in
seconds and, in this way, I was able to determine that, in my case, in my
tests, with a waiting time of 71 seconds a tunnel effect is generated, while,
with a waiting time of 72 seconds, it is not generated. Thus, according to my
results, the maximum tunneling time is 71 seconds.
I will now
present both tests.
CDC
Create an 'A' file in a folder; delete the 'A' file;
and recreate an 'A' file in the same folder
- Create a 512-byte 'A' file with a long name
- Delete the 'A' file
- Set a timeout of 71000 milliseconds
- Re-create a 512-byte 'A' file with a long name in
the same folder
In this test, as
you can see in the previous animated image, a file with the long name '512-71-LFN'
was created in the system in the 'Test' folder, on 11-06-2020 at 08:41:57. This
file was assigned the entry number 93893 in the MFT.
After waiting
300 seconds, the file with the name '512-71-LFN' was deleted and, after a wait
of 71000 milliseconds, another file of the same size was created again, in the
same folder, with the name '512-71-LFN'.
As you can see
from the above table extracts, the file '512-71-LFN', which occupied the entry
number 93893 in the MFT, has been deleted. Similarly, the file '512-71-LFN',
which occupies the entry 86001 in the MFT, has been created.
Regarding the
time stamps, the last file created, which occupies the entry number 86001, was
created on 11-06-2020 at 08:48:14. However, as you can see, by creating it with
the same file name as the previously deleted one, it acquires the creation date
of that deleted file, at 08:41:57, (in red), showing, in the other timestamps,
the original creation date of the file. This indicates that, in this case, with
a waiting time of 71000 milliseconds, a tunnel effect has been generated.
Create an 'A' file in a folder; delete the 'A' file;
and recreate an 'A' file in the same folder
- Create a 512-byte 'A' file with a long name
- Delete the 'A' file
- Set a timeout of 15000 milliseconds
- Re-create a 512-byte 'A' file with a long name in
the same folder
In this test, as
you can see in the previous animated image, a file with the long name
'512-72-LFN' was created in the system in the 'Test' folder, on 11-06-2020 at
08:50:27. This file was assigned the entry number 90575 in the MFT.
After waiting
300 seconds, the file with the name '512-72-LFN' was deleted and, after a wait
of 72000 milliseconds, another file of the same size was created again, in the
same folder, with the name '512-72-LFN'.
As you can see
from the above table extracts, the file '512-72-LFN', which occupied the entry
number 90575 in the MFT when the file was first created, still occupies the
same entry, with the same file name.
Regarding the time
stamps, the deleted file '512-72-LFN' was created on 11-06-2020 at 08:50:27,
creating again a file with the same name '512-72-LFN', after a waiting time of
72000 milliseconds, on 11-06-2020 at 08:56:37, presenting correctly the time
stamp of the creation of that file. This indicates that, in this case, with a
waiting time of 14000 milliseconds, no tunnel effect has been generated.
How do we explain that a tunnel effect has been
created?
Where should we
go when we find discrepancies in the time marks? Where can we explain that a
tunnel effect has occurred? The answer can be found in the '$LogFile'. The
'$LogFile' is a file that records all the changes that occur in a file and
therefore affect an NTFS volume. All changes involve all the metadata, the attributes,
of a file. Therefore, if we take into account that everything in an NTFS file
system is a file, we get that any action taken in the system will be recorded
in this log.
As you can see
in the table above, we have, on the one hand, that a file was created with the
name '4096_512_14_Seconds' on 02-06-2020 at 16:08:23, (in green). The file was
created in the folder assigned to the entry 92342 in the MFT, which corresponds
to the folder named 'Test'. The file was assigned the entry 93893 in the MFT. On
02-06-2020 at 16:13:23 the file '4096_512_14_Seconds', (in red), which had the
entry 93893 assigned in the MFT and which was located in the folder 'Test',
whose entry number in the MFT is 92342, was deleted. Again, a file was created
with the name '4096_512_14_Seconds', on 02-06-2020 at 16:13:37, (in green),
which was assigned the entry 93750 in the MFT. This last file was created in
the same 'Test' folder, whose entry in the MFT is number 92342.
On the other
hand, we have that the MFT entry with number 93893, which was previously
occupied by the file '4096_512_14_Seconds', was reassigned to the file
'he_settings.ini', on 02-06-2020 at 16:14:48, hosted in a different folder.
Conclusions
Some people
believe that file system tunneling does not have a strong impact on forensic
analysis. I believe it does. Why do I believe this? Because, if we are unable
to explain an event, how will we be able to find the answers to the questions
we are asking? If we are not able to explain how and why tunnel effects are generated,
how can we find the truth in our investigations?
There are
already times when understanding a timeline is very difficult. Understanding
this particularity, moreover, gives it one more handicap, because we have to be
able to spin one event with another, in order to provide a context for a
certain action.
I propose the
following example: You are performing a forensic analysis of a system where a
user had a certain content in a file. This user states that someone wanted to
frame him, changing the content of the file in question, (put here a content of
an illicit nature). In the analysis of the MFT you find only one reference to
that file, which has in the attributes of 'SI' and 'FN' the same date of
creation, although there are discrepancies in the other dates. If you do not
know this peculiarity of Windows systems, you will not be able to explain what
happened. If you cannot explain what happened, you cannot find the truth. And,
if you cannot find the truth, the user will be affected in the final result of
the analysis.
But come on,
that's just a curious opinion in this field of DFIR.
That's all,